Cybersecurity landscape is an ever-evolving battleground in this age of rapid digital transformation. Organizations must stay one step ahead of adversaries to protect digital infrastructures effectively. The National Security Agency and Cybersecurity and Infrastructure Security Agency have released cybersecurity advisory to highlight the most common cybersecurity misconfigurations and techniques to mitigate them.
In today’s rapidly evolving cybersecurity landscape, even a single misconfiguration can open up an entire organization to a vast array of vulnerabilities. Security misconfigurations occur when system settings are improperly adjusted or essential security protocols are omitted, leaving systems open to attacks. These configuration errors often happen in cloud environments, network setups, applications, or databases, each representing potential entry points for cyber threats. With misconfigurations cited as one of the leading causes of data breaches and unauthorized access incidents, they are a significant area of concern in digital security. This risk is especially pronounced in cloud environments, where the growing complexity and integration of services can introduce a web of configurations. Cloud misconfigurations, such as open storage buckets, overly permissive access controls, and inadequate encryption, often go undetected until exploited. For organizations that rely on cloud services to support remote work, customer engagement, and core business operations, the potential for security misconfigurations grows exponentially with each new service or application added. As cloud adoption accelerates, understanding and addressing security misconfigurations is crucial. Organizations of all sizes must be proactive in managing configurations to protect their infrastructure and data from potential threats. This article highlights the ten most common misconfigurations, as identified by the NSA and CISA, and offers practical techniques to mitigate these risks, empowering organizations to build resilient cybersecurity defenses.
Default Configurations of Software and Applications
When software and applications are installed, they often come with default settings designed for ease of use. Unfortunately, these pre-set configurations are not always optimized for security. Default settings may include weak passwords, unnecessary features, open ports, enabled guest accounts, excessive permissions, publicly accessible management interfaces, and insecure SSL/TLS configurations.
Mitigation: The first step in securing software and applications is to change all default usernames and passwords immediately after installation. Disable any unnecessary features and services, close unneeded ports, and tighten file permissions. Management interfaces should never be publicly accessible without additional security layers, such as IP restrictions or VPNs.
Improper Separation of User and Administrator Privileges
Allowing users to have administrative privileges unnecessarily can lead to serious security risks. This misconfiguration occurs when users are granted more access than required for their roles, or when administrators do not properly secure their accounts. Such accounts often have widereaching access, making it easier for attackers to move laterally across the network with a compromised credential.
Mitigation: Enforce the principle of least privilege (PoLP), ensuring that users only have the access they need to perform their job functions. Administrators should use dedicated, secured accounts for system administration tasks and avoid using them for everyday activities. Regular reviews of access permissions are essential to ensure that roles are correctly assigned.
Insufficient Internal Network Monitoring
Without sufficient monitoring of internal network activities, suspicious events can go unnoticed for extended periods, allowing attackers to operate undetected. This lack of oversight can lead to the compromise of sensitive data, malware infections, or unauthorized access to systems, which can remain unaddressed until it’s too late.
Mitigation: Deploy comprehensive internal monitoring tools that provide real-time alerts for suspicious activities. Network traffic should be continuously analyzed for abnormal patterns, and any anomalies should be investigated immediately. Organizations should implement intrusion detection and prevention systems (IDPS) to ensure prompt responses to potential threats.
Lack of Network Segmentation
Network segmentation is a critical security measure that divides a network into isolated segments to prevent attackers from moving freely across the network. Without proper segmentation, attackers who gain access to one part of the network can easily move to other systems, increasing the risk of data breaches and insider threats.
Mitigation: Segment the network based on roles and functions, ensuring that sensitive areas (such as databases or production environments) are separated from user and public-facing areas. Utilize firewalls, VLANs, and access control lists (ACLs) to enforce strict communication rules between network segments. Implement zero-trust principles where every network access request is verified, regardless of origin.
Poor Patch Management
Patch management is crucial for addressing known vulnerabilities in software and systems. However, many organizations fail to apply patches in a timely manner, leaving their systems vulnerable to attacks. Unpatched systems are often easy targets for attackers using publicly available exploits.
Mitigation: Implement an automated patch management process that regularly checks for updates and applies patches as soon as they are available. Prioritize patches based on the severity of vulnerabilities and maintain an accurate inventory of all software and systems to ensure that nothing is overlooked. Organizations should also avoid using unsupported software or hardware, as they no longer receive security updates.
Bypass of System Access Controls
Attackers can bypass access controls through methods such as brute force attacks, phishing, or using stolen credentials. This allows them to gain unauthorized access to systems and sensitive data. Weak access control mechanisms, especially in third-party applications, often exacerbate this risk.
Mitigation: Implement strong password policies that require complex, unique passwords, and enforce multi-factor authentication (MFA) across all accounts. Regularly audit and update access controls to ensure they remain effective against evolving threats. Centralized identity management solutions can help enforce consistent access control policies across all systems and applications.
Weak or Misconfigured Multi-Factor Authentication (MFA)
While MFA provides an additional layer of security, misconfigurations or weak implementations can still leave systems vulnerable to attacks. Allowing insecure fallback options, such as SMS-based authentication, or not enforcing MFA across all user accounts, reduces its effectiveness.
Mitigation: Ensure that MFA methods are robust and resistant to common attacks such as phishing or SIM swapping. Organizations should consider using more secure options like appbased authenticators or hardware tokens. MFA should be enforced for all users, particularly for privileged accounts and remote access.
Insufficient Access Control Lists (ACLs) on Network Shares and Services
ACLs define who can access certain resources on a network. If not properly configured, unauthorized users may gain access to sensitive data, modify files, or even take control of systems. Poor ACL configurations on network shares are a common target for attackers.
Mitigation: Carefully configure ACLs to restrict access to sensitive resources. Ensure that only authorized users can access network shares and services, and regularly audit ACL settings for vulnerabilities. Use role-based access control (RBAC) models to simplify the management of permissions.
Poor Credential Hygiene
Many organizations suffer from poor credential hygiene, including the use of weak passwords, password reuse, and storing passwords in plaintext. These practices make it easier for attackers to gain access to systems, especially if MFA is not enabled.
Mitigation: Enforce strong password policies, requiring complex and unique passwords for each account. Implement a password management solution to help users securely store and manage their credentials. Regularly rotate passwords, and never store them in plaintext.
Unrestricted Code Execution
Unrestricted code execution occurs when attackers can run arbitrary code on a target system. This can happen through vulnerabilities such as buffer overflows, SQL injection, or crosssite scripting (XSS). Attackers often exploit system drivers or use scripting languages to execute malicious activities without triggering security alerts.
Mitigation: Regularly update and patch all software to prevent exploitation of known vulnerabilities. Use web application firewalls (WAFs) and input validation to protect against SQL injection and XSS attacks. Restrict the use of executable files and scripting languages to trusted sources, and regularly monitor for suspicious activities related to code execution.
Conclusion
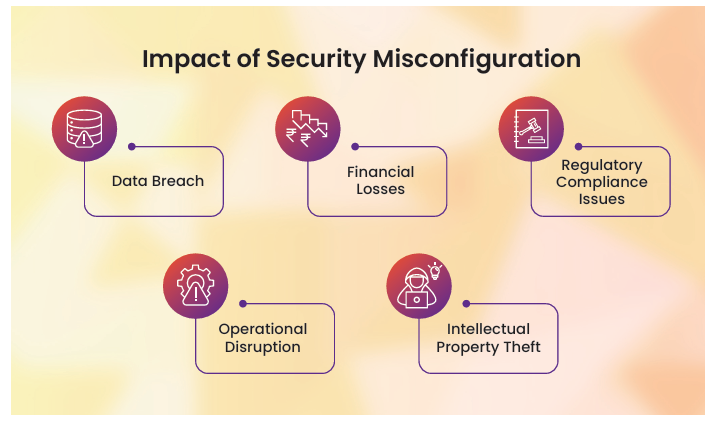
Misconfigurations are among the leading causes of cybersecurity breaches Addressing them proactively can significantly reduce the risk of compromise. By following best practices such as enforcing access control, implementing MFA, establishing effective patch management, and configuring ACLs properly, organizations can bolster their defenses against cyberattacks. Continuous monitoring, regular audits, and proactive configuration management are essential steps in maintaining robust security configurations. Ultimately, mitigating cybersecurity misconfigurations requires vigilance and a proactive approach to manage digital infrastructure effectively. Organizations that prioritize security settings and take preventative measures are better equipped to safeguard their networks and data from evolving threats. This proactive stance not only protects vital information but also enhances an organization’s reputation, ensuring trust and reliability among its clients and stakeholders.
Contributors / Authors

R. Bindu MadhaviScientist- D r.bindumadhavi@nic.in
- Tag:
- Internet
- Technology
- eGov
- Tech
State Informatics Officer
NIC, Tamil Nadu State Centre
E2-A, Rajaji Bhavan, Besant Nagar
Chennai, Tamil Nadu - 600090